Showing posts with label hack. Show all posts
Showing posts with label hack. Show all posts
8 best tools to break through the Wi-Fi networks and get the password in Kali Linux
Way to penetrate Wi-Fi most of the stuff in search of a way to penetrate after Facebook accounts! , Perhaps the latter may be difficult more than the first, as we know very well that you can easily break through the router devices for various reasons, first, in terms of the gaps that usually will not release an update in a lot of these devices, or because of poor password already. Or other reasons that do not disappear, we dear supervisor. In this post you will learn together the best tools to penetrate wireless networks in Kali Linux system.
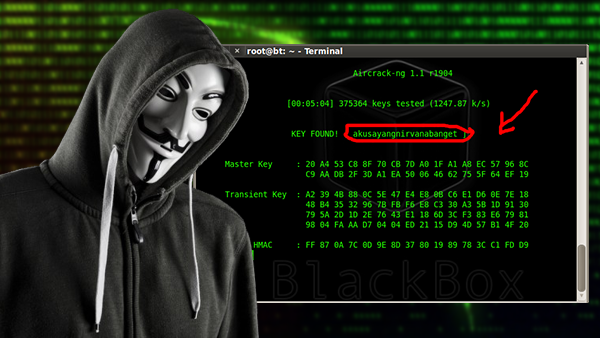
1 Aircrack-ng
It is the most popular tools in this area, and no doubt you will find a number of articles that explain how they operate in addition to a set of videos that you can take advantage of them and learn from them. The gadget contains a host of other utilities to break Wi-Fi network of the type of WPA / WPA2 / WEP.
2 Reaver
Of good as well as the tools and specialized in exploiting a loophole in WPS technology in the most of modern router. It is also to help you protect your network from this dangerous gap that usually do not pay attention to it.
3 Pixiewps
A new tool has been added to the Linux distribution recently, this tool as well as exploiting a loophole "WPS", you guess the number "PIN" using all available algorithms also supports many of the router devices.
4 Wifite
Of the unique things about this tool is that it is doing all the work is automatic, making it easier for you to work with the tool. You can use it to break the encryption with WEP, WPA or WPA2 networks, but with activating the WPS, as you also work four-way-handshake in the case of the networks WPA or WPA2 if you do not activate WPS.
5 Fern Wifi Cracker
This tool is not like all the other tools that are often adopted on the command line, but what distinguishes this tool as it comes graphical interface where you can be used by anyone who is used like a normal program in Windows.
6 Wash
If you want to break any router using a loophole "WPS", the first thing you should know is whether the router is infected this gap? is not it ! Yes, this tool role is to determine whether the activation of "WPS" in the router device to be breached.
7 Crunch
A common way to get through the Wi-Fi networks are mainly relying on the dictionary, which includes hundreds of thousands of random words and tested to get the password for the router. This is known as the attack "brute force", this tool role is to generate "wordlists" custom that can be used to launch such attacks.
8 Macchanger
In some cases may be available on a password for a particular network, but will not be surprised that you can contact them, and the reason that the owner of the network filtering devices are allowed to connect through the mac address. This tool also referred her work is the basic change your Mac Idriss device in order to fool the router. Method is also useful in the case was used NetCut program to disconnect you.
Labels:
hack
Pirated movie traced to Hollywood executive as trove of unreleased films leak online
A plethora of top movies were leaked online this week, many of which are yet to be released in cinemas. Included in the leak was a copy of Quentin Taratino’s The Hateful Eight, which was uploaded first.
According to The Hollywood Reporter, the actual leak have been tracked to be able to the owner of the actual DVD screener, Tim Kosove, co-CEO regarding Alcon Activity.
Kosove seemed to be directed a content of a ‘screener’ regarding honors factor, but the delivery seemed to be brought in regarding through an office asst. This content seemed to be followed to be able to him via an inserted watermark identified within when it was uploaded to be able to piracy sites across the World-wide-web.
Needless to say, Kosove states he’s “never witnessed this particular DVD” knowning that “it’s never ever handled [his] fingers. ” Because of this, he’s working together with the particular FBI as well as launching an indoor study straight into where by it may have come by.
Your motion picture ended up being saved hundreds of thousands of that time period as it ended up being submitted this few days and the group behind the launch had attemptedto eliminate the watermark prior to expressing the video.
Each year screener reports involving films drip on to bittorrent web sites ahead of merit events, because the agencies at the rear of impending movies circulate early on reports to a bigger team intended for concern, regardless of whether the actual flick can be nevertheless for being introduced.
It is not clear after that eventually Kosove in the short term, though THR reviews in which he’s working with the particular FBI to determine chain involving guardianship to the DVD immediately after this achieved this company.
➤ ‘Hateful Eight’ Pirated Screener Traced Back to Top Hollywood Executive [THR]
➤VIA: THENEXTWEB
Xbox gaming platform subjected to a violent attack by pirates!
Is the Phantom Squad group and one of the intruders pirates who target a wide range of giant companies and the overthrow of the various global services, and for some reason have not been announced officially been hacker group so-called Phantom Squad had revealed earlier this year that it will launch a a series of attacks on the Xbox platform service subsidiary of Microsoft, and this has been a declaration issued by the hackers group Phantom Squad as a frank and direct threat to the giant Microsoft Corp. and rich from the definition.
And despite the fact that the pirates Phantom set Squad threat of Microsoft Corp. in advance that Microsoft, however, the company may have fallen victim to pirates where the pirates to launch a series of cyber attacks on the Xbox service games platform which led to the establishment of Microsoft Corp. to stop temporarily the service to have been resolved technical problems related to the security and protection of the podium with the assurance that the service will be launched as soon as possible again.
And of the complex problems of the Xbox platform for the Games, a subsidiary of Maakosowic is that they are not at all available at good or strong security system that protects the platform Xbox games, although it is among the largest gaming platforms in the world and the most widespread, and from the point of the pirates of view by News in circulation at the present time, the Phantom Squad group targeting the Xbox platform and attack them until the Microsoft platform to provide high-potential protection system protects the platform and its users.
And for hackers hackers, the cyber attacks on the gaming platform X Facebook will remain constant to be Microsoft's company will be able to fend off these attacks and secure gaming platform Xbox, and some experts have was surprised in the field of security and protection of Microsoft Corp. because they could not repel the arrest of the pirates and Xbox service although the Microsoft of the strongest global companies and richest financially attacks.
Numerous conflicts combine piracy and international companies, and to communicate more about the latest technology news of what is happening in the world of technical and informational You only need to visit a blog site constantly to stay informed on various subjects renewable permanently.
And despite the fact that the pirates Phantom set Squad threat of Microsoft Corp. in advance that Microsoft, however, the company may have fallen victim to pirates where the pirates to launch a series of cyber attacks on the Xbox service games platform which led to the establishment of Microsoft Corp. to stop temporarily the service to have been resolved technical problems related to the security and protection of the podium with the assurance that the service will be launched as soon as possible again.
And of the complex problems of the Xbox platform for the Games, a subsidiary of Maakosowic is that they are not at all available at good or strong security system that protects the platform Xbox games, although it is among the largest gaming platforms in the world and the most widespread, and from the point of the pirates of view by News in circulation at the present time, the Phantom Squad group targeting the Xbox platform and attack them until the Microsoft platform to provide high-potential protection system protects the platform and its users.
And for hackers hackers, the cyber attacks on the gaming platform X Facebook will remain constant to be Microsoft's company will be able to fend off these attacks and secure gaming platform Xbox, and some experts have was surprised in the field of security and protection of Microsoft Corp. because they could not repel the arrest of the pirates and Xbox service although the Microsoft of the strongest global companies and richest financially attacks.
Numerous conflicts combine piracy and international companies, and to communicate more about the latest technology news of what is happening in the world of technical and informational You only need to visit a blog site constantly to stay informed on various subjects renewable permanently.
Serious on Facebook new loophole threaten your accounts! Beware!
A few hours ago I received an alert on Facebook (Notification) as a person of my friends has identified in the comments, and by simply pressing the alarm turned my browser to a new page containing the video and the page is very similar to the Facebook page, and fortunately were true habit I always what I look at the website link at the transition from page to page so I discovered that I turned to another site completely, and asked me to the site that focused even add video runs with me.
Personally, I consider this a very serious gap in terms of conversion and easy way for any novice in the world of the Internet and the world of private protection. Tunisian Global Protection Team Tunisian WhiteHat Security As for the addition, which invites page to her inauguration has assured me that once installed on your browser will automatically receive an invitation at least 200 people from the list of your friends for a specific URL (often the same location, which turned to him) through the use of system alarm on Facebook.
The gap was not famous yet, so in the opinion it takes some time could be a week until Facebook is addressing her and closed but in case you want to protect yourself against them is recommended that you pass the mouse button on the alarm and that I noticed that the alarm will make a transfer you to another site as shows that's at the bottom it is best to avoid lack of pressure on him.
In the case of previously signed into the trap of this gap and the inauguration of you added it is recommended that you remove the direct addition of the browser along with the word Facebook Secret change.
Subscribe to:
Posts (Atom)